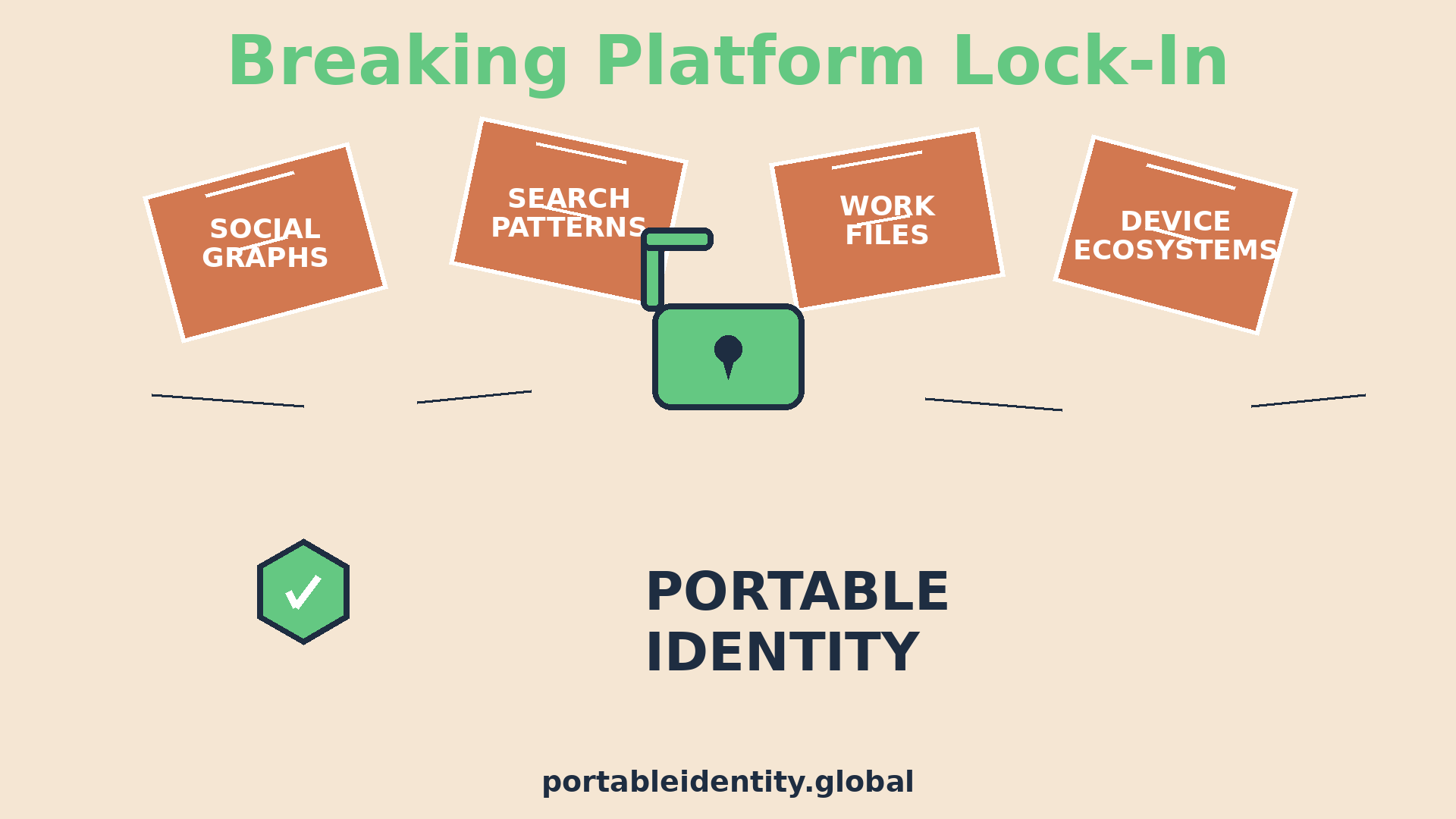
The Verification Monopoly
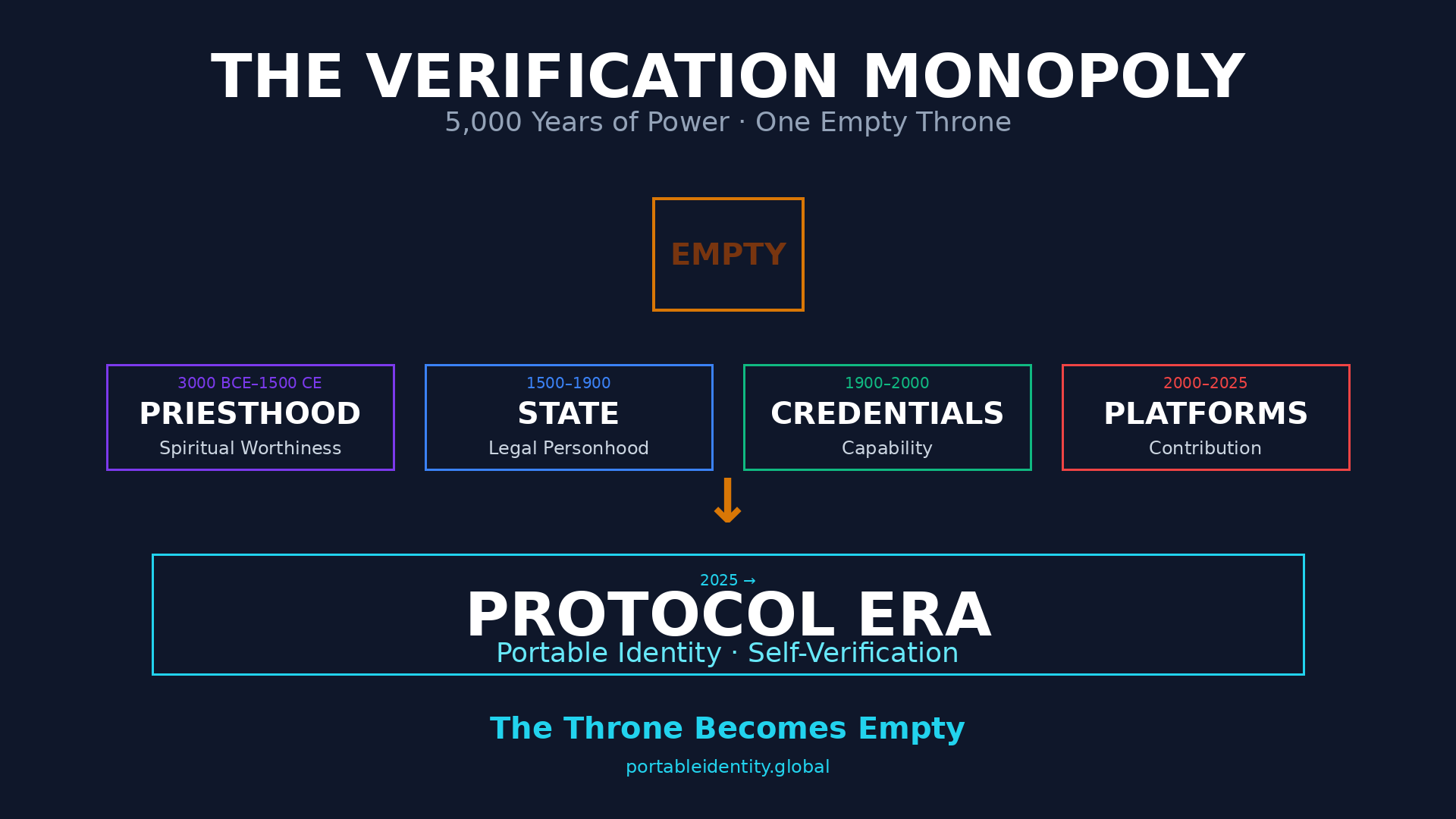
Who Gets to Say What’s True: The 5,000-Year Power Structure That Portable Identity Destroys For 5,000 years, power belonged to whoever could say: ”This is true about you—and you cannot prove otherwise.” Priests verified your spiritual worthiness. States verified your legal existence. Universities verified your capability. Employers verified your value. Banks verified your trustworthiness. Platforms … The Verification Monopoly