Who Gets to Say What’s True: The 5,000-Year Power Structure That Portable Identity Destroys
For 5,000 years, power belonged to whoever could say: ”This is true about you—and you cannot prove otherwise.”
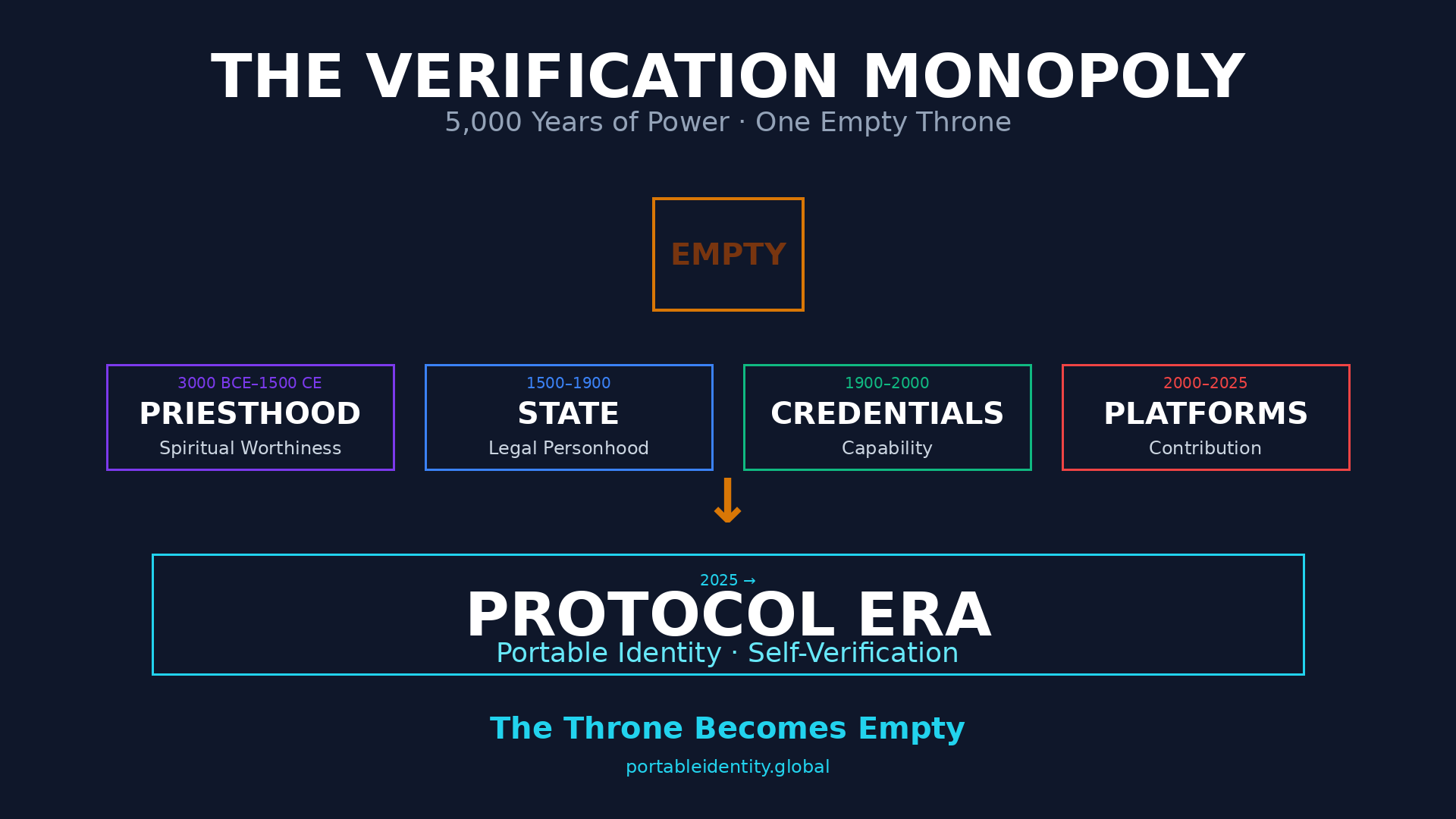
Priests verified your spiritual worthiness. States verified your legal existence. Universities verified your capability. Employers verified your value. Banks verified your trustworthiness. Platforms verified your contributions.
Different faces of the same monopoly: verification.
The power to declare what counts as evidence. The power to certify identity, capability, value, trustworthiness. The power to say ”this is legitimate proof” and ”this is not.”
Institutions did not derive power from creating value. They derived power from controlling verification of value. Not from possessing truth, but from monopolizing what counts as evidence of truth.
The throne of verification is the invisible source of all institutional power.
And in 2025, that throne becomes empty.
Not through revolution. Through information architecture. Through a technical shift that makes verification monopoly structurally impossible for the first time in human history.
Portable Identity + ContributionGraph + MeaningLayer invert the information asymmetry that made institutional verification monopoly necessary. When you possess more complete information about yourself than any institution possesses about you, verification becomes self-evident rather than institutionally controlled.
This is not about better identity systems. This is not about platform competition. This is about the collapse of civilization’s foundational power structure—and what replaces it.
THE THREE MECHANISMS OF CAPTURE
Every institution maintains verification monopoly through three structural mechanisms:
1. Exclusive Evidence Creation
Only institutions can create the evidence they require. You cannot give yourself a degree, credit score, or platform reputation. The evaluator controls the evaluation. This creates permanent information asymmetry.
2. Evidence Format Control
Your proof must speak institutional language—or it doesn’t exist. Testimonials don’t count as credentials. Verified outcomes don’t count as metrics. Evidence legibility is controlled, not just evidence creation.
3. Verification Persistence Denial
When you leave, your verified status vanishes. Your degree persists, but the actual evidence—problems solved, understanding demonstrated, growth achieved—remains locked in institutional records you cannot access or transport.
Together: You cannot prove things about yourself without institutions, cannot format proof without institutional blessing, and cannot transport proof when you leave.
This is not incidental. This is the architecture that makes institutional power possible.
THE PATTERN ACROSS 5,000 YEARS
Priesthood Era (3000 BCE–1500 CE): Religious institutions monopolized verification of spiritual worthiness. You could live virtuously, demonstrate wisdom, help others—but only priests could certify your relationship with the divine. Spiritual status determined social position, legal rights, economic opportunity. The church controlled heaven—and through that control, governed earth.
State Era (1500–1900): Governments monopolized verification of legal personhood. You could exist physically, participate in society, create value—but only states could certify you as legal person with rights. Birth certificates, passports, citizenship papers became gates to property ownership, legal protection, political participation. The state controlled legal existence—and through that control, governed citizens.
Credential Era (1900–2000): Universities monopolized verification of capability. You could master skills, solve problems, demonstrate expertise—but only credentials could certify competence. Degrees, licenses, certifications became gates to employment, professional practice, economic advancement. Academia controlled capability recognition—and through that control, governed opportunity.
Platform Era (2000–2025): Digital platforms monopolized verification of contribution. You could create value, help people, build knowledge—but only platform metrics could certify it mattered. Followers, engagement, reputation scores became gates to visibility, influence, economic participation. Platforms controlled value recognition—and through that control, governed digital civilization.
The structure never changed across 5,000 years:
New domain emerges → institutions claim exclusive authority to verify status in that domain → society accepts this as natural because no alternative exists → institutions extract value by controlling access to verification → power concentrates in verification authorities.
The content changed. The costume changed. The monopoly remained constant.
You could not challenge verification when institutions controlled the only systems capable of producing verification. You could not prove spiritual worthiness without church records. You could not prove legal existence without state documents. You could not prove capability without academic credentials. You could not prove contribution without platform metrics.
Verification monopoly is the load-bearing column of institutional power across all of human civilization.
And that column is collapsing.
THE INVERSION
Why Verification Created Power
Power never came from knowing truth. Power came from controlling what counts as evidence of truth.
A university doesn’t need to know whether you’re capable—it needs only to control the certification employers require. Its power derives from monopoly over capability certification, not accuracy of capability assessment.
Institutional power is indifferent to truth. Institutional power cares only about verification monopoly.
This worked because of one foundation: information asymmetry.
For 5,000 years, institutions possessed more complete information about you than you could access about yourself. Not because they were smarter, but because they controlled the systems that recorded, aggregated, and formatted information about human capability and value.
When you graduate, the university retains: which problems you solved, how you approached challenges, where you demonstrated understanding, what you struggled with, how you grew over time.
You receive: a certificate with a number on it.
The institution possesses the evidence. You possess a summary score.
This asymmetry was technically unavoidable—until now.
What Portable Identity Actually Disrupts
Portable Identity doesn’t compete for verification authority.
Portable Identity eliminates verification as an institutional function.
Before: You solve a problem. They benefit. Value is created. But proof exists in three forms: your memory (unreliable), their memory (private), platform record (trapped, proprietary, losable). To prove this mattered requires institutional verification.
After: You solve a problem. They benefit. Value is created. Proof exists in one form: cryptographically-signed attestation from the beneficiary in your ContributionGraph, semantically located in MeaningLayer, portable across every context forever.
The contribution proves itself. No institution required. No verification monopoly possible.
The Completeness Inversion
For the first time in human history, you possess more complete information about yourself than any institution possesses about you.
Previously:
- Universities knew your complete academic record. You knew your grades.
- Employers knew your complete work history. You knew your job titles.
- Banks knew your complete financial behavior. You knew your credit score.
Institutions possessed the comprehensive record. You possessed the summary.
With Portable Identity + ContributionGraph + MeaningLayer:
You possess:
- Every verified contribution you’ve ever made
- Every capability cascade you’ve created
- Every attestation from every beneficiary
- Complete semantic context for every contribution
- Cryptographic proof of every claim
- Continuous record across all platforms, all contexts, all time
Institutions possess:
- Fragments within their domain
- Metrics that measure engagement, not meaning
- Snapshots without continuity
- Platform-specific data without portability
The information asymmetry inverts. Permanently.
And with it, the power structure inverts.
Why AI Makes This Inevitable
AI agents require complete, continuous, semantically-rich identity to function. Fragmented institutional verification makes AI agents blind.
An AI agent acting on your behalf needs your complete value graph: verified expertise across every domain, contribution history across every platform, reputation across every context, complete capability demonstration record.
Incomplete information = worthless information in the age of AI.
Users migrate to platforms where AI agents can access complete portable identity—because those agents are dramatically more capable. Platforms maintaining verification monopoly over fragments lose users to platforms integrating with complete portable identity protocols.
The competitive dynamics are irreversible: completeness wins, fragmentation dies.
THE EXISTENTIAL THREAT
Every institution whose power derives from verification monopoly faces existential threat—not business model threat, not competitive threat, but existential threat.
Universities exist to verify capability. When individuals prove capability through verified contribution cascades, universities lose their reason for existing.
Employers exist to assess capability. When individuals possess complete verified records with cryptographic proof, employers cannot assess better than the record itself.
Banks exist to verify trustworthiness. When individuals possess comprehensive records of value creation and commitment fulfillment, banks cannot assess creditworthiness better than the contribution graph.
Platforms exist to measure contribution. When individuals own portable contribution graphs with semantic location and cascade tracking, platforms cannot measure better than the graph itself.
Why Resistance Is Inevitable
When existence depends on verification monopoly, threats to that monopoly trigger maximal defense:
Legal barriers: Licensing requirements mandating institutional certification. Professional regulations prohibiting self-verification.
Epistemological attacks: ”Self-verification cannot be trusted.” ”Portable identity enables fraud.” ”Institutional verification ensures quality.”
Technical sabotage: Proprietary standards fragmenting portability. Platform policies prohibiting external verification. API restrictions preventing data aggregation.
Social delegitimization: ”Only our graduates are truly educated.” ”Only our platforms measure real contribution.”
This is not conspiracy. This is structural necessity. Existential threats trigger existential defense.
Why Resistance Cannot Succeed
Completeness beats fragmentation. A credential says ”This person passed our tests.” A complete contribution graph says ”This person solved these specific problems for these specific people with these specific verified outcomes and cascade effects over this time period with cryptographic attestation from every beneficiary.” Proof beats claims.
Continuity beats snapshots. An institutional assessment says ”This person had this capability at this moment.” A continuous contribution graph says ”This person has demonstrated sustained capability growth across these domains over these years with this trajectory.” Evidence beats evaluation.
Cascades beat metrics. An institutional reputation says ”This person has X followers, Y engagement.” A verified contribution graph with cascade tracking says ”This person enabled these specific individuals who then enabled these individuals in verifiable chains with measurable capability increases at each node.” Impact beats activity.
When proof competes with claims, proof wins. The information asymmetry has inverted.
FROM GATEKEEPERS TO SERVICE PROVIDERS
Institutions face binary choice:
Option A: Maintain verification monopoly. Resist portable identity. Defend information asymmetry.
Result: User exodus to institutions integrating with portable identity. Network effects work against you. Death by irrelevance.
Option B: Abandon verification monopoly. Integrate with portable identity infrastructure. Compete on value created rather than certification controlled.
Result: Survival through transformation.
Service provider institution: An organization that creates genuine value for individuals without claiming exclusive authority to verify that value was created.
Universities become capability enablers, not certifiers. They compete on how much capability increases while working with them—proven through students’ contribution graphs showing actual problem-solving, knowledge transfer, and cascade effects. Value measured by outcomes, not grades.
Employers become impact enablers, not assessors. They compete on how much capability grows and how many cascades are created while working there—tracked through employees’ portable contribution records. Talent proven by verified contributions, not performance reviews.
Banks become capital enablers, not judges. They compete on terms offered based on borrowers’ verified records of value creation and commitment fulfillment—shown through complete contribution history. Creditworthiness proven by track record, not proprietary score.
Platforms become collaboration enablers, not measurers. They compete on how easily users create verified contributions and enable cascades—integrated with users’ portable graphs. Value flows to users, not trapped in platform metrics.
The fundamental shift: from ”We certify you” to ”We enable you to prove yourself.”
From monopoly to utility. From gatekeeper to infrastructure. From extraction to enablement.
The institutions that integrate first capture network effects. The institutions that resist last face extinction.
THE NEW INFRASTRUCTURE
When verification monopoly collapses, what replaces it is protocol-layer verification infrastructure.
Portable Identity eliminates verification as an institutional function and establishes it as protocol-layer infrastructure accessible to everyone, controlled by none.
Three architectural elements make this possible:
Portable Identity: Cryptographic infrastructure binding your identity to your complete contribution history, portable across every platform and institution. Not controlled by any entity. Protocol-layer infrastructure enabling verification without intermediaries.
ContributionGraph: Complete record of every verified contribution—every problem solved, person helped, capability transferred, cascade created. With cryptographic attestation from beneficiaries, semantic location showing contribution type, temporal continuity showing growth, cascade tracking showing multiplication effects. Peer-verified, cryptographically-signed, semantically-located proof of impact.
MeaningLayer: Semantic infrastructure making human value machine-legible without reducing it to metrics. Not ”X engagement” but ”Y type of understanding that led to Z capability increases in these domains for these people.” Enables AI to understand significance, not just count activity.
Together: verification infrastructure that is complete, continuous, portable, unfakeable, and semantic.
This is constitutional infrastructure—as fundamental to digital civilization as voting systems are to political participation. When verification shifts from institutions to protocols, the infrastructure enabling that verification becomes a fundamental right.
You cannot prove you exist as conscious being without portable identity infrastructure. You cannot prove your capability without contribution graph infrastructure. You cannot prove your value without meaning layer infrastructure.
Rights require infrastructure. Verification infrastructure for human dignity must be neutral protocol, not proprietary product.
This is why portableidentity.global must remain neutral infrastructure—accessible to all, controlled by none, surviving any institutional failure.
THE DECLARATION
The throne of verification is empty.
For 5,000 years, institutions possessed more complete information about you than you could access about yourself. This asymmetry made verification monopoly technically necessary and institutionally inevitable.
That era ends now.
With Portable Identity + ContributionGraph + MeaningLayer, you possess more complete, continuous, semantically-rich, cryptographically-verified information about yourself than any institution can access about you.
The information asymmetry inverts. The power structure inverts. The verification monopoly collapses.
This is not destruction. This is evolution—from gatekeepers to service providers, from monopoly to utility, from institutional assessment to protocol-layer verification.
Institutions that recognize this transition will survive by competing on value created rather than certification controlled. Institutions that resist will die through network effects as users migrate to completeness.
Resistance is inevitable but futile. Completeness beats fragmentation. Continuity beats snapshots. Proof beats claims. The market routes value to better information.
AI agents require complete, continuous, semantically-rich identity. Users prefer platforms where their AI agents work better. The competitive dynamics are irreversible.
The window for early integration is closing. First movers capture network effects. Late movers face existential crisis.
The ability to prove your capability, your value, your contributions, your existence as conscious being—these are fundamental rights in digital civilization. And rights require infrastructure.
Portable Identity is not a product. It is protocol-layer infrastructure for human dignity.
The throne of verification is empty. Not because institutions abandoned it—because the technology that made that throne necessary has been superseded by technology that makes it obsolete.
Power no longer derives from controlling what counts as evidence. Power derives from enabling individuals to create unfakeable evidence about themselves.
The verification monopoly is ending. Not someday. Now. Not theoretically. Structurally. Not through fighting institutions—through information symmetry that makes institutional verification obsolete.
Welcome to the post-verification era.
Where proof replaces claims. Where completeness beats fragments. Where protocols replace monopolies. And where the power to say ”this is true about you” belongs to you—cryptographically, semantically, portably, permanently.
About This Article
This essay examines the verification monopoly—the 5,000-year power structure where institutions maintained authority by controlling what counts as evidence about human capability, value, and identity. It demonstrates why Portable Identity, ContributionGraph, and MeaningLayer collectively eliminate verification as an institutional function, why this transition is inevitable through information asymmetry inversion, and why institutional resistance cannot prevent the collapse of verification monopoly.
The analysis operates across five layers simultaneously: historical (tracing verification monopoly across civilizational eras), epistemological (examining who determines truth), economic (showing how value extraction follows from verification control), technical (demonstrating why completeness beats fragmentation), and evolutionary (explaining institutional natural selection through adaptation).
This is not about better identity systems. This is about the collapse of civilization’s foundational power structure through protocol-layer verification infrastructure that makes institutional verification technically obsolete for the first time in human history.
Rights and Usage
All materials published under PortableIdentity.global are released under Creative Commons Attribution-ShareAlike 4.0 International (CC BY-SA 4.0).
Right to Reproduce: Anyone may copy, quote, translate, or redistribute this material freely, with attribution to PortableIdentity.global.
Right to Adapt: Derivative works are explicitly encouraged, as long as they remain open under the same license.
Right to Defend the Definition: Any party may reference this framework to prevent private appropriation, trademark capture, or proprietary redefinition of protocol-layer concepts.
No exclusive licenses will ever be granted. No commercial entity may claim proprietary rights over Portable Identity.
Verification infrastructure is public infrastructure—not intellectual property.
Source: PortableIdentity.global
Date: November 2025
Version: 1.0